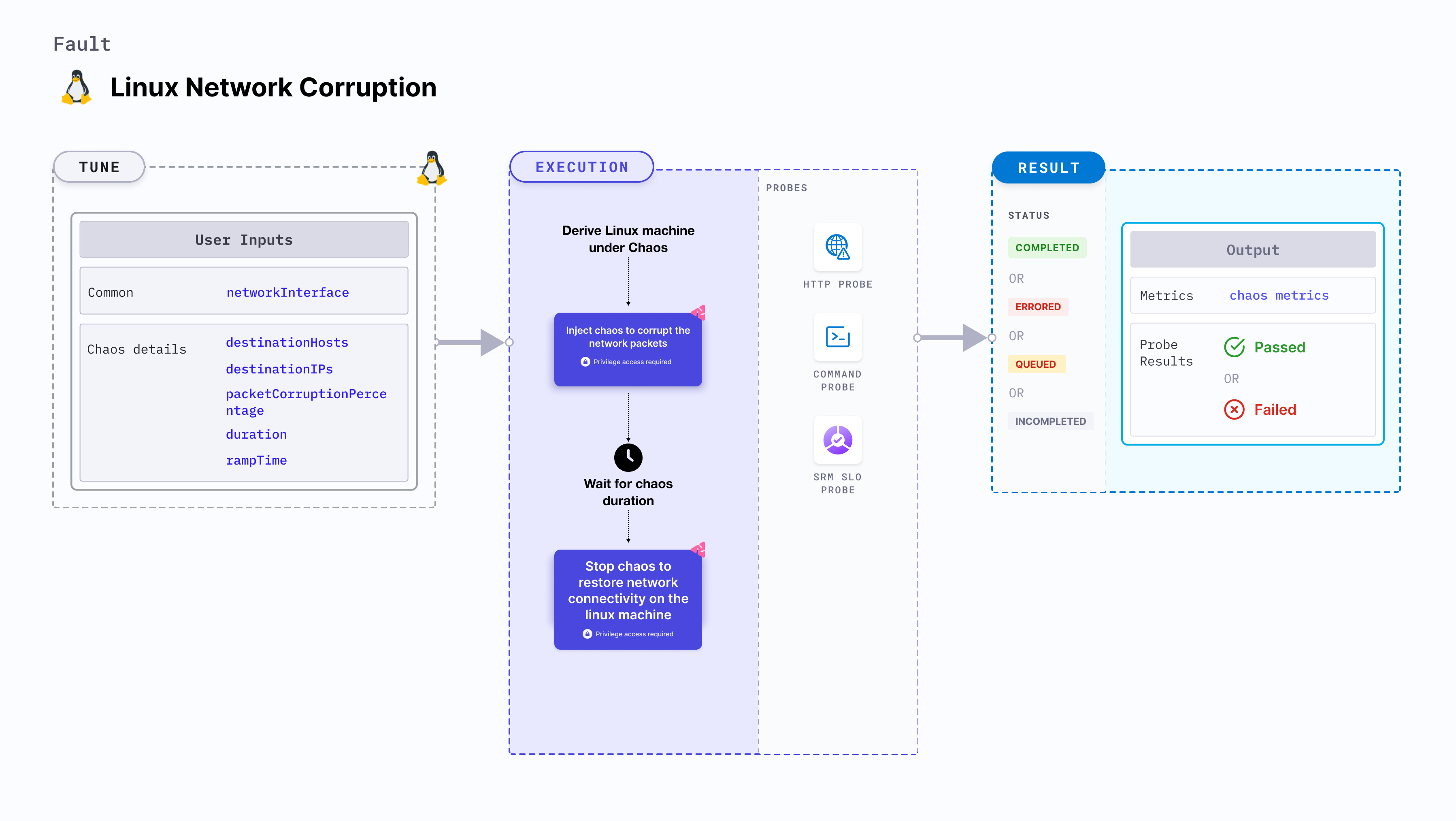
Linux network corruption
Linux network corruption injects chaos to disrupt network connectivity by corrupting the network requests on a Linux machine.
Use cases
Linux network corruption:
- Induces network corruption on the target Linux machines.
- Simulates network corruption by corrupting responses to incoming requests on the machine.
- This fault can be executed on Ubuntu 16 or higher, Debian 10 or higher, CentOS 7 or higher, RHEL 7 or higher, Fedora 30 or higher, and openSUSE LEAP 15.4 or higher.
- The
linux-chaos-infrastructuresystemd service should be in an active state, and the infrastructure should be inCONNECTEDstate.
Fault permissions
The fault uses the root Linux user and root user group.
Mandatory tunables
| Tunable | Description | Notes |
|---|---|---|
| networkInterfaces | Comma-separated values of target network interfaces. | For example, eth0,ens192 |
Optional tunables
| Tunable | Description | Notes |
|---|---|---|
| destinationHosts | List of target host names or keywords. For example, google.com,litmuschaos.io | If neither destinationHosts nor destinationIPs is present, the fault injects chaos for all host names/domains. |
| destinationIPs | List of comma-separated target IPs. Also supports a list of target destination ports for a given IP, that are separated by a pipe (|). For example, 1.1.1.1,35.24.108.92|3000|8080. | If neither destinationHosts nor destinationIPs is provided, all host names/domains are targeted. |
| packetCorruptionPercentage | Percentage of packets to corrupt. For example, 50 . | Default: 100 % |
| sourcePorts | Source ports to be filtered for chaos. For example, 5000,8080 | Alternatively, the ports can be whitelisted, that is, filtered to be exempt from chaos. Prepend a ! to the list of ports to be exempted. For example, !5000,8080 |
| destinationPorts | Destination ports to be filtered for chaos. For example, 5000,8080 | Alternatively, the ports can be whitelisted, that is, filtered to be exempt from chaos. Prepend a ! to the list of ports to be exempted. For example, !5000,8080 . |
| duration | Duration through which chaos is injected into the target resource. Should be provided in [numeric-hours]h[numeric-minutes]m[numeric-seconds]s format. | Default: 30s. Examples: 1m25s, 1h3m2s, 1h3s |
| rampTime | Period to wait before and after injecting chaos. Should be provided in [numeric-hours]h[numeric-minutes]m[numeric-seconds]s format. | Default: 0s. Examples: 1m25s, 1h3m2s, 1h3s |
Destination hosts
The destinationHosts input variable subjects the comma-separated target host names to chaos.
The following YAML snippet illustrates the use of this input variable:
apiVersion: litmuchaos.io/v1alpha1
kind: LinuxFault
metadata:
name: linux-network-corruption
labels:
name: network-corruption
spec:
networkChaos/inputs:
destinationHosts: 'google.com'
networkInterfaces: "eth0"
Destination IPs
The destinationIPs input variable subjects the comma-separated names of the target IPs to chaos. You can specify the ports to be targeted for an IP by using a pipe (|) as a separator. Providing ports is optional, omitting them will affect all the ports associated with the destination IPs.
The following YAML snippet illustrates the use of this input variable:
apiVersion: litmuchaos.io/v1alpha1
kind: LinuxFault
metadata:
name: linux-network-corruption
labels:
name: network-corruption
spec:
networkChaos/inputs:
destinationIPs: '1.1.1.1,192.168.5.6|80|8080'
networkInterfaces: "eth0"
Source and destination ports
By default, the network experiments disrupt traffic for all the source and destination ports. Tune the interruption of specific port(s) using sourcePorts and destinationPorts inputs, respectively.
sourcePorts: Ports of the target application whose accessibility is impacted.destinationPorts: Ports of the destination services or pods or the CIDR blocks(range of IPs) whose accessibility is impacted.
The following YAML snippet illustrates the use of this input variable:
apiVersion: litmuchaos.io/v1alpha1
kind: LinuxFault
metadata:
name: linux-network-corruption
labels:
name: network-corruption
spec:
networkChaos/inputs:
destinationIPs: '1.1.1.1'
networkInterfaces: "eth0"
sourcePorts: "8080,3000"
destinationPorts: "5000,3000"
Ignore source and destination ports
By default, the network experiments disrupt traffic for all the source and destination ports. Ignore the specific ports using sourcePorts and destinationPorts inputs, respectively.
sourcePorts: Provide source ports that are not subject to chaos as comma-separated values preceded by!.destinationPorts: Provide destination ports that are not subject to chaos as comma-separated values preceded by!.
The following YAML snippet illustrates the use of this input variable:
apiVersion: litmuchaos.io/v1alpha1
kind: LinuxFault
metadata:
name: linux-network-corruption
labels:
name: network-corruption
spec:
networkChaos/inputs:
destinationIPs: '1.1.1.1'
networkInterfaces: "eth0"
sourcePorts: "!8080,3000"
destinationPorts: "!5000,3000"
Packet corruption percentage
The packetCorruptionPercentage input variable corrupts a specific percentage of data packets.
The following YAML snippet illustrates the use of this input variable:
apiVersion: litmuchaos.io/v1alpha1
kind: LinuxFault
metadata:
name: linux-network-corruption
labels:
name: network-corruption
spec:
networkChaos/inputs:
packetCorruptionPercentage: '50'
networkInterfaces: "eth0"